We're excited to announce a major expansion to the Hacker Sidekick platform with 6 powerful new security tool integrations now available to all users. These additions significantly enhance your reconnaissance, threat intelligence, and security research capabilities—all accessible through our familiar AI chat interface.
What's New
Shodan Integration Suite
The world's most comprehensive internet search engine is now fully integrated into Hacker Sidekick with three specialized tools:
Shodan Search Toolkit - Discover internet-connected devices, identify exposed services, and map attack surfaces across global infrastructure. Perfect for asset discovery and reconnaissance phases of security assessments.
Shodan DNS Toolkit - Perform advanced DNS intelligence gathering, subdomain discovery, and infrastructure mapping. Essential for understanding target organization DNS footprints and relationships.
Shodan Metadata Helper - Get expert guidance on crafting effective Shodan searches with intelligent suggestions and search optimization. Ensures you're getting maximum value and comprehensive results from your reconnaissance efforts.
Passive Intelligence Tools
Certificate Transparency Integration - Leverage Certificate Transparency logs for passive subdomain discovery and certificate monitoring. Perfect for stealth reconnaissance through SSL/TLS certificate data analysis.
AbuseIPDB Integration - Check IP reputation and threat intelligence from the community-driven database. Essential for incident response, threat hunting, and security operations center workflows.
Have I Been Pwned Integration - Access breach intelligence and password exposure data for security awareness and risk assessment. Understand your organization's exposure in historical data breaches.
How to Access Your New Tools
Getting started with these integrations is simple—they're all accessible through natural conversation with Hacker Sidekick:
Note: These tool integrations are currently available through the web chat interface. They are not accessible when using Hacker Sidekick agentically or through API integrations (such as in Roo Code).
Step 1: Start a New Chat
Navigate to your Hacker Sidekick dashboard and start a new conversation. The tools are automatically available—no additional setup required for most integrations.
Tool Management: You can easily enable or disable specific tools using the plus (+) menu located on the left side of the chat input box. This gives you complete control over which integrations are active for each conversation, allowing you to customize your toolkit based on your current research needs.
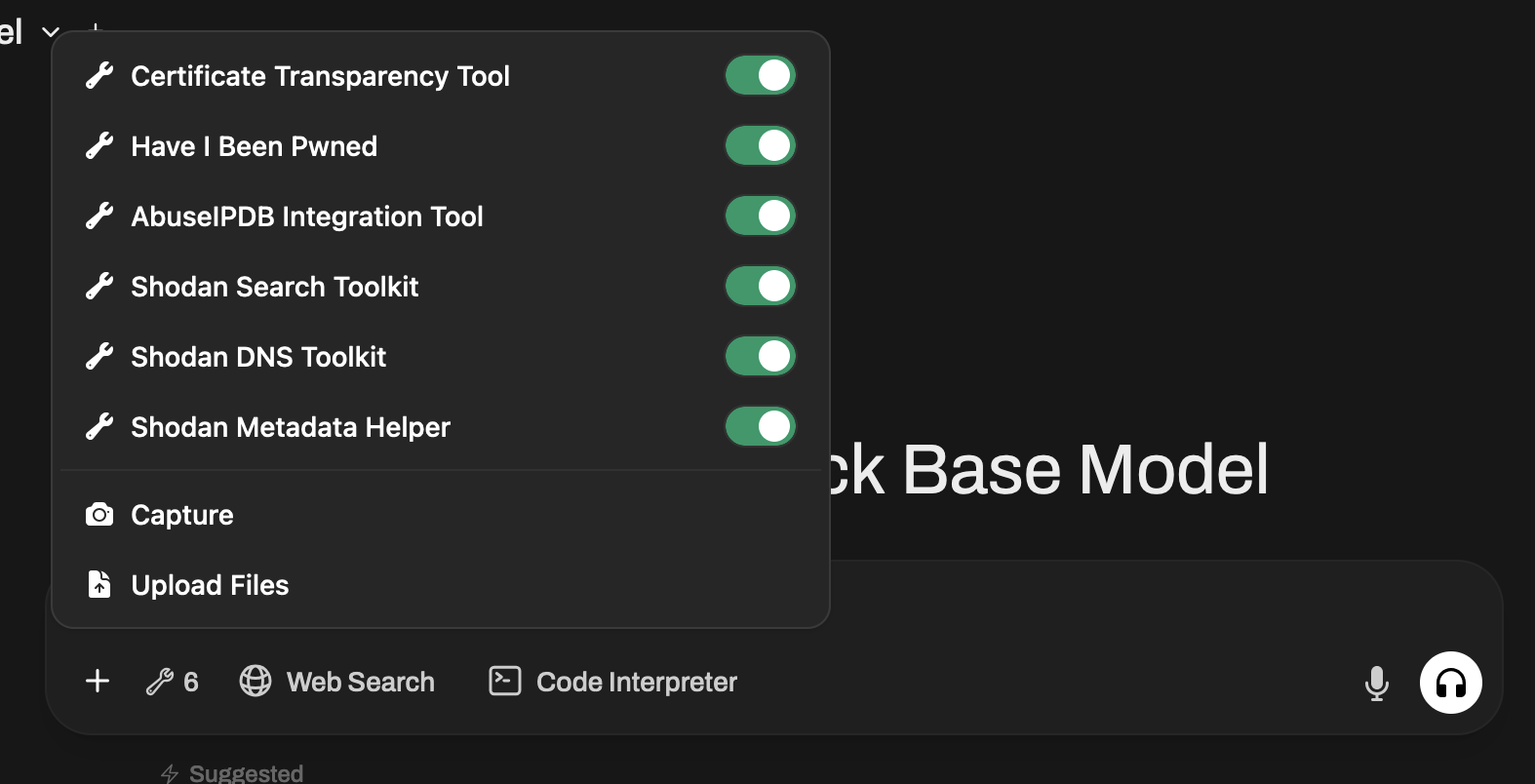
Step 2: Use Natural Language Commands
Simply describe what you want to investigate. Here are some example prompts to get you started:
For Shodan searches:
- "What internet-facing assets can you find for example.com?"
- "Search Shodan for vulnerable Apache servers"
- "Find exposed databases using Shodan"
For passive reconnaissance:
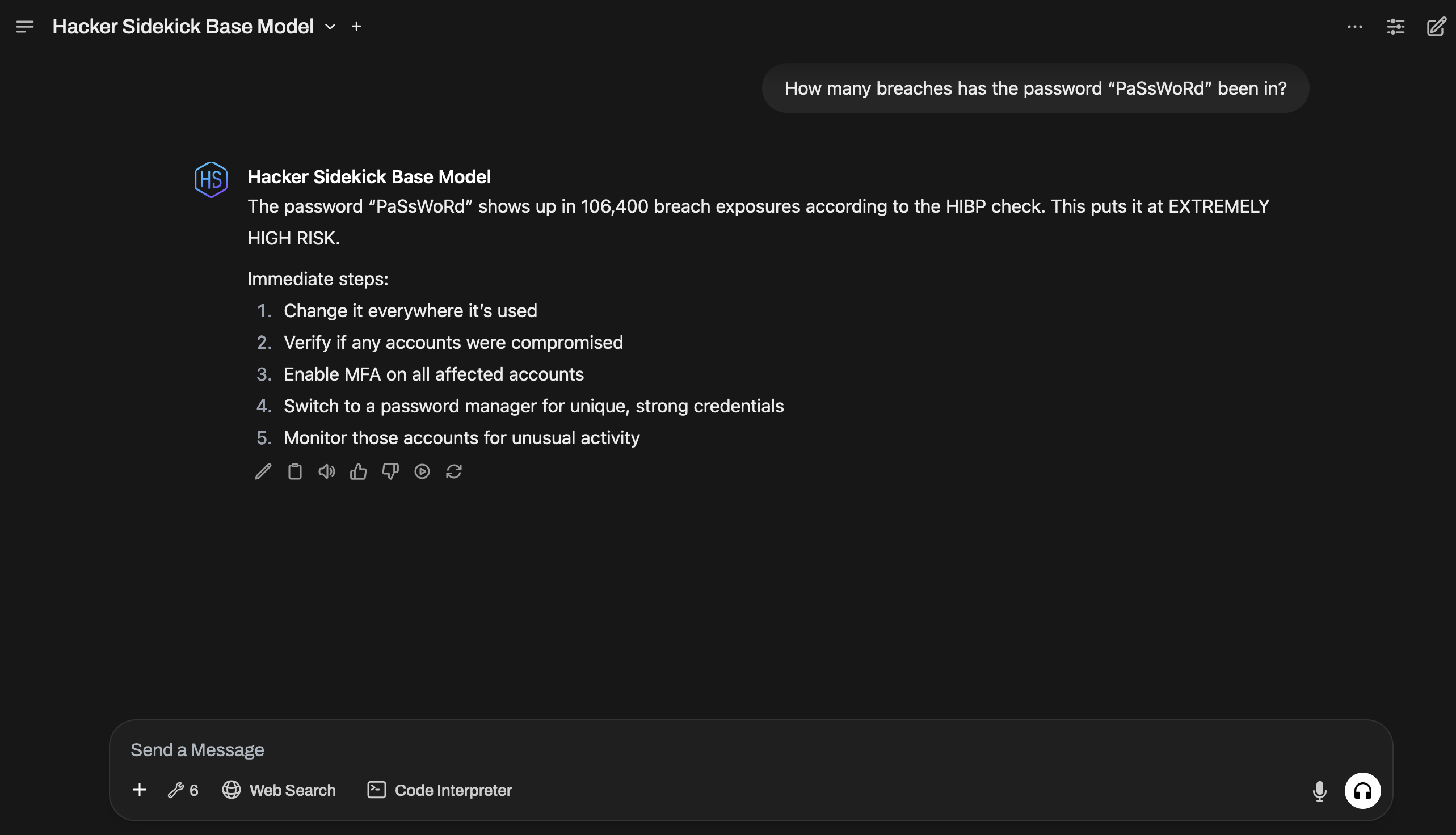
- "Find subdomains for target-company.com using certificate transparency"
- "Check the reputation of IP address 192.168.1.100"
- "Has our company domain been involved in any data breaches?"
Real-World Applications
These new integrations unlock powerful workflows for security professionals:
Bug Bounty Hunters can now discover expanded attack surfaces by combining Shodan reconnaissance with certificate transparency subdomain discovery, then validate findings with reputation checks.
Incident Responders can quickly assess IP addresses using AbuseIPDB, understand breach exposure through Have I Been Pwned, and gather infrastructure intelligence via Shodan DNS tools.
Penetration Testers can conduct comprehensive reconnaissance using the full Shodan suite, while Certificate Transparency provides passive discovery options that won't trigger defensive systems.
Security Operations Teams can enhance threat hunting with reputation data and breach intelligence, while Shodan tools provide ongoing asset discovery and monitoring capabilities.
Security & Ethics
All integrations follow responsible disclosure practices and include built-in guidance for ethical usage. Hacker Sidekick reminds users to:
- Only test systems you own or have explicit permission to assess
- Follow platform terms of service and usage guidelines
- Use intelligence for defensive purposes and authorized security testing
- Follow applicable laws and regulations in your jurisdiction
Get Started Today
These new integrations are available immediately to all Hacker Sidekick users at no additional cost. Simply log in to your account and start exploring these powerful new capabilities through natural conversation.
New to Hacker Sidekick? Sign up for free and get instant access to all integrations, plus our comprehensive cybersecurity AI assistant.
Questions about the new tools? Our AI can help you understand capabilities, suggest optimal usage patterns, and troubleshoot any issues. Just ask: "How do I use the new Shodan integrations?"
What's Next
This expansion represents our commitment to providing security professionals with the most comprehensive AI-powered platform available. We're continuously working on additional integrations and capabilities to enhance your security operations.
Have a security tool you'd like to see integrated? Let us know through the feedback option in your dashboard—we're always listening to our community's needs.
Ready to supercharge your security research? Start using the new integrations now →